The Blog deals with the day to day modern Hacking techniques used by Hackers to harm Systems. You may also get Some Knowledge regarding Android, and other Mobile OS and Also the Day to Day Technology trends going in outside arena ! :)
Sunday, 3 August 2014
Saturday, 12 July 2014
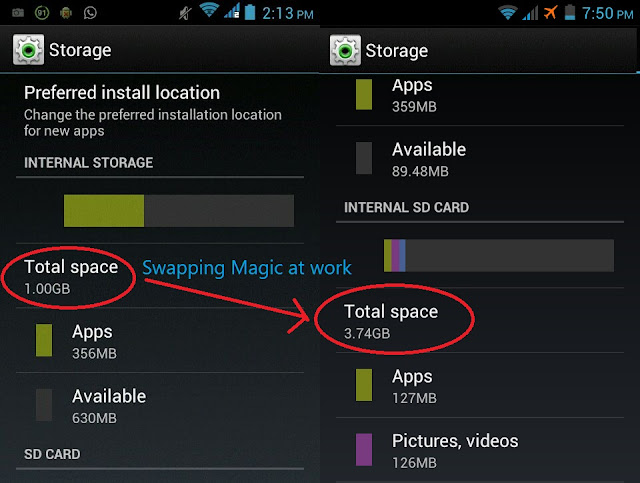
Easiest way to Swap any Android's External sd and Internal. :)
Requirements :-
- A rooted Android (If your Android is not rooted than read this - Rooting Android )
- Root Explorer
- Some Brain.
These days, a lot of Android phones and tablets with internal storage of 1 Gigabyte or more are partitioned by default into two parts:
- Phone's internal storage: Stores system apps, other system files.
- Internal sdcard: Stores apps data, sd data in case of heavy games. Basically it works similar to what a normal sdcard works to on every other phones that comes with such partitions.
Guide: Swapping your internal and external sdcard
- First of all, you must have a rooted Android as mentioned earlier. If your Android is not rooted then Root it easily by following the steps given here : How to root your Android.
- Now Download and install Root Explorer. You can download the cracked version at : Root Explorer 3.1.7 apk
- Open Root Explorer and go through this file located at :

- Mount the Directory as read and write (R/W)
- Open "void.fstab"
- Look for these lines and make these changes-
- “dev_mount sdcard /mnt/sdcard” and change it to “dev_mount sdcard /mnt/ extsd”
- "dev_mount extsd /mnt/extsd” and change it to “dev_mount extsd /mnt/ sdcard”
Make sure that you only make changes to the word “sdcard” and “extsd” and nothing else. This will show the internal memory as external memory and the external (SD card) as internal memory.
Once done, save this file and go back to Root Explorer.
- A backup file named “void.fstb.bak” will be automatically created. Delete this file by pressing hold the file and select delete. Close the Root Explorer app.
- Switch off the Phone and switch it back on. Go to Settings then storage and check internal storage. Your internal memory memory will become external card storage and external storage will become Internal memory.
Ask me if u have any Queries.
© Programmed Hackers ;)
Sunday, 23 February 2014
Changing Administrator Password using Command Prompt (CMD) !
After reading this post, you’ll be able to change your(or anyone’s) Administrator account password in windows 7, without asking him the previous one. Usually, for changing the passwords, we go to User Accounts in Control Panel and then opt for changing the passwords. But windows doesn't permit us to do so, till we enter the previous password.
So, it’s clear that we can’t change the password from this method. Because, the current password is also required here, which we don’t know.
But, the same thing can become possible, if perform the same task through Windows Command Prompt (CMD). In this method, we are not prompted to enter the current/old password. But for that, we first need to be logged in as an Administrator (see step 2 below), unless you will be shown an error message stating “System 5 Error”. So, I don’t want you to get this “System 5 Error”, that’s why I was focusing on this point. This hack is very easy, you are only required to perform my all steps, in the exact manner. If you still get any problem, then you can drop your comments below this post.
The steps are as follows :-
Step-1 :- Press start, and search CMD (windows command prompt).
Step-2 :- Now, do right click on CMD and select RUN AS ADMINISTRATOR(it’s the most important step of this hack, unless “System 5 Error” will be shown in the end) and then click OK. Most of the users don’t read the whole sentence and press Enter right after searching CMD in this step. Those users get an error named “System 5 Error”. So, please don’t press Enter directly on CMD.
This hack only works when you’re logged in to the Administrator(or administrator like) account. This hack need Administrator(or administrator like) privileges, unless it shows “System 5 Error”. This hack is thus NOT POSSIBLE if you are logged in with the GUEST ACCOUNT.
This hack only works when you’re logged in to the Administrator(or administrator like) account. This hack need Administrator(or administrator like) privileges, unless it shows “System 5 Error”. This hack is thus NOT POSSIBLE if you are logged in with the GUEST ACCOUNT.
Step-3 :- Now type the command NET USER and press ENTER It will give u the names of all the USER A/C’s existing in your computer.
Step-4 :- Here, in this pic, you are getting three names, which are Kamesh, Vaibhav and Guest. We are not at all interested in the Guest account for sure. So leave that. Now the two accounts are left. One is Kamesh and the other is Vaibhav. Here, the both the accounts are having admin priviledges. In most of the cases the main admin account, which is ‘Kamesh’ here, is hidden. And the other account, named ‘Vaibhav’ here, is shown, which is a ADMIN-LIKE account. So, this account also have full admin priviledges. Because only one admin account which is visible here is ‘Vaibhav’, so we will deal with this account in this process.
So, now use our next command, which is net user Vaibhav *
Here, there’s ONE SPACE between NET and USER as well as between Vaibhav and *
Here, there’s ONE SPACE between NET and USER as well as between Vaibhav and *
Step-5 :- Here u are, now directly enter the new ADMINISTRATOR PASSWORD and press enter again confirm ur new password and press enter. You will not see any ************* type of characters in the CMD window when you will be typing your password. But you don’t worry. They are not visible but they got typed. Re-type the same password in Confirm Password option.
Step-6 : U are done. Just type EXIT and then press ENTER to exit. That’s all
Sunday, 16 February 2014
Hacking A Computer Using Fastrack on Backtrack.
Requirments :
1. Backtrack
2. IP address of victim.
3. Brain.
Now follow these steps :
1. Open Fastrack by clicking on Applications-->Backtrack-->Exploitation tools-->Network exploitation tools-->Fast-Track-->fasttrack-interactive.
7. If you get any open ports then enter it like in image.
8. After that type 3 to select Executable and hit enter, this option will create a executable file in directory filesystem-->pentest>exploit-->fasttrack-->payload.exe.
9. Now the send executable file to victim and when the victim open this file you will be connected to computer remotely.
Share if u find Useful ! :)
© Programmed Hackers :)
1. Backtrack
2. IP address of victim.
3. Brain.
Now follow these steps :
1. Open Fastrack by clicking on Applications-->Backtrack-->Exploitation tools-->Network exploitation tools-->Fast-Track-->fasttrack-interactive.
2. Now after opening fastrack select the option Payload generator by typing 8 and hitting enter.
3. Now after that type 1 to select Windows Shell Reverse_TCP and hit enter.
4. Now after that type 2 to select shikata_ga_nai and hit enter.
5. Now after that enter the IP address of victim and hit enter.
6. Now you have to scan IP address to get open ports. (Google regarding it)
6. Now you have to scan IP address to get open ports. (Google regarding it)
7. If you get any open ports then enter it like in image.
8. After that type 3 to select Executable and hit enter, this option will create a executable file in directory filesystem-->pentest>exploit-->fasttrack-->payload.exe.
9. Now the send executable file to victim and when the victim open this file you will be connected to computer remotely.
Share if u find Useful ! :)
© Programmed Hackers :)
Thursday, 6 February 2014
SQL Injection Using SqlMap (Backtrack 5 R3)
Sqlmap Is An Automated Pen Testing Tool. That Automates The Process Of Detecting And Exploiting SQL Injection Flaws And Taking Over Of Databases. It Comes With A Powerful Detection Engine, Many Niche features For The Ultimate Pen Tester And A Broad Range Of Switchs Lasting From Database Fingerprinting. Over Data Fetching From The Database. This Tool Is Best For Beginners. Who Just Now Entered In Security Field. It Is Easy To Use Tool. This Tool Makes SQL Injection Easy As Compared To Manual SQL Injection.
Follow these simple steps to hack website using backtrack 5 sqlmap tool.
1. Open your backtrack terminal and type cd /pentest/database/sqlmap and hit enter. Now sqlmap is open in your terminal
2. Now find the vulnerable site. (well I already have vulnerable site). You can search for vulnerable sites using Dorks. Google it!
4. Now you will get the database name of the website
7. Now you will get the tables list which is stored in aj database.
Now we got the columns and we got username and password
Now just find the admin panel of the website and use proxy/vpn when you are trying to login in the website as a admin
© Programmed Hackers :)
Follow these simple steps to hack website using backtrack 5 sqlmap tool.
1. Open your backtrack terminal and type cd /pentest/database/sqlmap and hit enter. Now sqlmap is open in your terminal
2. Now find the vulnerable site. (well I already have vulnerable site). You can search for vulnerable sites using Dorks. Google it!
3. Now type this command in the terminal and hit enter.
4. Now you will get the database name of the website
Well I got the two database aj and information_schema we will select aj database.
5. Now get the tables of that database. for that you need to enter this command into your terminal and simply hit Enter.
python sqlmap.py -u http://yourvictim’slink/index.php?id=4 -D (database name) –tables
6. Now we need to grab the tables from the aj database. paste this command bellow command and hit enter.
python sqlmap.py -u http://www.yourvictim’slink.com/index.php?id=4 -D aj –tables
7. Now you will get the tables list which is stored in aj database.
8. Now lets grab the columns from the admin table
python sqlmap.py -u http://www.yourvictim’slink.com/index.php?id=4 -T admin –columns
Now we got the columns and we got username and password
9. Now lets grab the passwords of the admin
Now we got the username and the password of the website !python sqlmap.py -u http://www.yourvictim’slink.com/index.php?id=4 -T admin -U test –dump
Now just find the admin panel of the website and use proxy/vpn when you are trying to login in the website as a admin
© Programmed Hackers :)
Saturday, 1 February 2014
Hydra (Brute Force Attack) to Hack any E-mail Password !
A password attack that does not attempt to decrypt any information, but continue to try different passwords. For example, a brute-force attack may have a dictionary of all words or a listing of commonly used passwords. To gain access to an account using a brute-force attack, a program tries all available words it has to gain access to the account. Another type of brute-force attack is a program that runs through all letters or letters and numbers until it gets a match.
How to do Brute force or (Dictionary Attack)
So here we are going to use Backtrack 5, Hydra Attack. I will use fake G-mail a/c for this tutorial
Requirements.
- Backtrack 4 or 5 with Internet connection
- Password.txt file (That contains Possible passwords)
- Brain.
I took fake ID of G-mail (hackerseven5@gmail.com) as my victim it's password is '521478963', and Suppose i know the possibilities of password so, I will make password.txt file to do brute force attack like this >
Now it's time to start attack using Hydra gtk.
Go to > Application > Backtrack > Privilege Escalation > Password Attacks > Online Attacks > hydra-gtk.
Fill all info on hydra-gtk like this way :-
* Single Target = smtp.gmail.com
* Port = 465
* Protocol = smtp
* mark = Use SSl, Be Verbose, Show Attempts
After setting your Target, go on Password tab >
Fill all info in this way !!
* Username = G-mail ID (hackerseven5@gmail.com)
* Password list = upload your possibilites password file
(save your password.txt file on desktop)
After all go to > Start Tab and Clik on Start.
So, your Brute Force Attack has been started :-
After all it will try Brute force attack using every password and try to login
with possibilities password, if you were lucky !! then it will show successful message like this.
Friday, 31 January 2014
3 Must Read Hacking Books for no0bs as well as pro's :)
1) Metasploit the Penetration testers guide
2) Backtrack 5 Wireless Penetration testing
3) The Hacker's Underground Handbook - D. Melnichuk (2008) WW.1
Download here : https://www.mediafire.com/?z840vpv2zujm5km
© Programmed Hackers
Wednesday, 29 January 2014
Hacking a Facebook account using Phishing !
# What is Phishing ?
Phishing is a fake login page designed by an attacker to steal personal info of victim's. Phishing page looks same as Original page of any website or social networking website.
# How Phishing works ?
As, I told you Phishing is a fake login page that is well designed same as original page to steal personal info of victim's for eg. (ID, Password, E-mail, Contacts, Credit Card Stealing, etc).
An attacker will create a fake login page and host it on any free web hosting sites and attacker will send link of fake page to victim to steal his personal info or data and when victim will provide his personal info such as E-mail ID or Password then victim's E-mail and Password will be stole and get hacked.
# How to Prevent and save us from Phishing attack ?
Well !! it is easy to detect any Phishing page.
1. Use best Antivirus and update it daily
2. Check URL before logging to any website.
4. Beware of E-mail Spoofer.
# How to Create Phishing page and Hack any A/c ?
So, Friends here is our main topic, how to create Phishing page and hack any E-mail, Password :D
1) Here, I take Facebook as my Fake Page to hack Facebook ID's
2) Download Facebook Phishing page from here [Download] (Latest Updated)
3) Create free a/c on 000webhost.com and get free domain
4) Here, I had already created one a/c for tutorial
5) After creating free a/c and domain go to your Control panel > and Click on File Manager
6) If it will ask for password, then provide your Password
7) And then go in public_html folder and delete default.php file
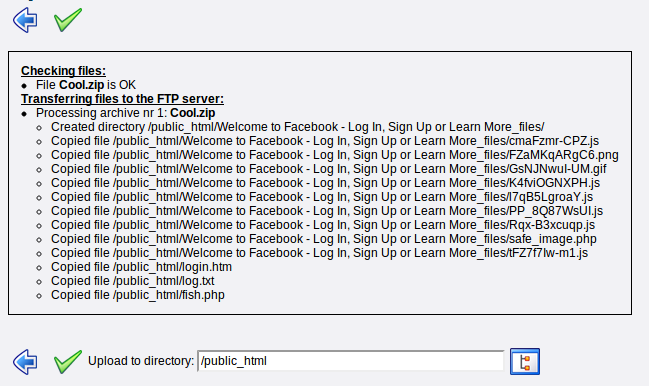
8) After deleting default file, click on upload and you will be redirected to this page
9) I suggest you to use ZIP archives to upload it's fast and easy :D, so click on choose file
and select ZIP file you downloaded it step 2.
10) After uploading your Phishing page you will see this page
10) After uploading your Phishing page you will see this page
11) So after all type your Domain name in Address bar hit enter and you'll get fake fb login page.
12) And now copy the Address of this page and Go to Google URL Shortener and
Shortern your URL to make your victim's Fool and not to detect as SPAM
13) Let's check whether our Phishing page is working or not ? Go on your Phishing page
and Enter any fake ID and Password in E-mail and Password BOX
14) After providing your fake info click on login and you will be redirected to original fb login page
and victim E-mail ID and Password will be logged.
and victim E-mail ID and Password will be logged.
15) How to know the Password ? Again Go to your 000webhost dashboard and
over there you will see anotther file manager
16) Go in Another file manager > public_html > After Entering in public_html folder you will see this 4 files -
17) Double click on log.txt file and download it after all open it !! hahahaha !!
18) WOW !! Here you can see how Phishing attack works and steal FB password. Enjoy
Like us on Facebook : Programmed Hackers
Subscribe to:
Posts (Atom)

















.png)



+4+(1).png)








.png)

